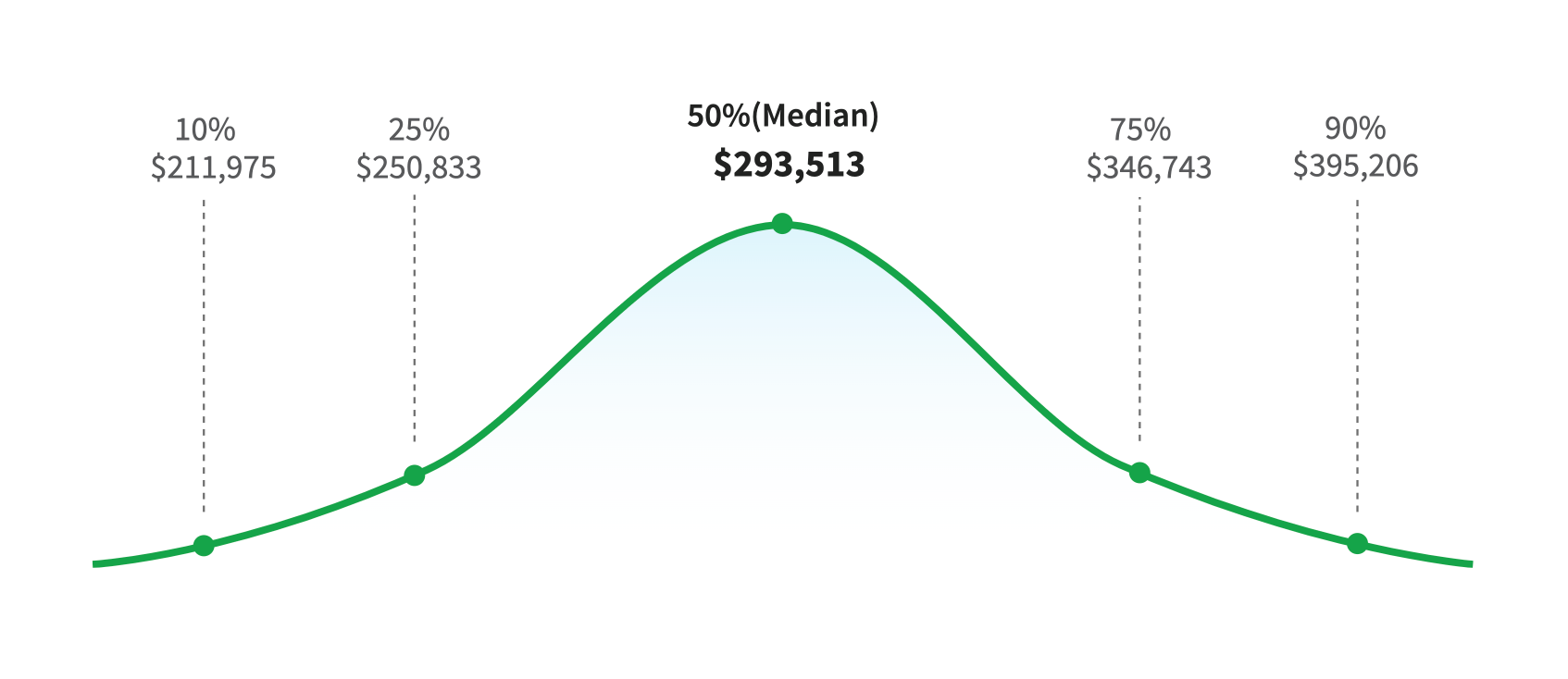
The annual compensation for a full-time Chief Information Security Officer (CISO) averages over $292,000*. For many small and medium-sized businesses (SMBs), this cost can significantly surpass their budget constraints. However, virtual Chief Information Security Officer (vCISO) service emerges as your cost-effective solution. Say goodbye to hefty expenses; our vCISO will be your savior, offering top-notch cybersecurity expertise without breaking the bank. Discover how our tailored vCISO services can safeguard your organization efficiently and affordably.



